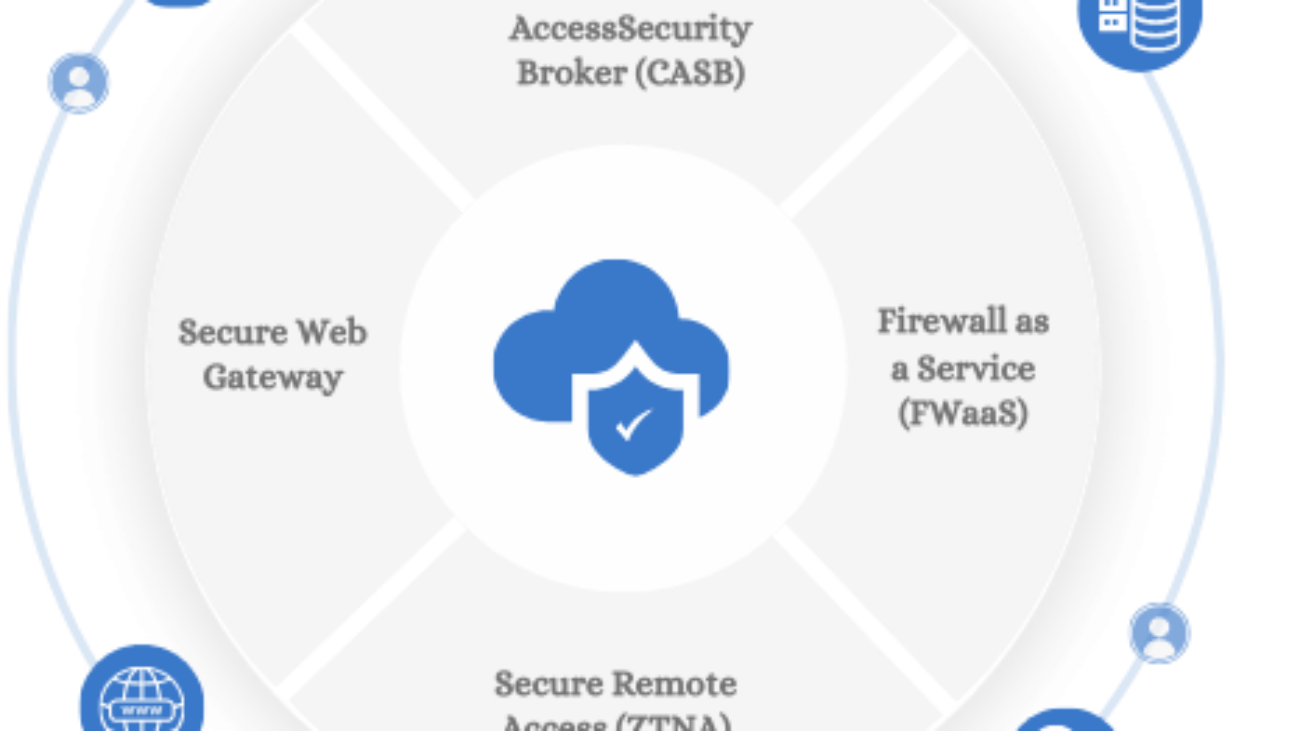
Zero Trust Implementation
Versa ensures secure, seamless connectivity for your users to both SaaS and private applications by implementing least privilege access policies and continuous trust evaluation. This approach minimizes risk by granting only the necessary access based on real-time assessments, enhancing both security and user experience.
Enhancing Security for SaaS and Private Applications
In today’s evolving cyber threat landscape, securing both SaaS and private applications is more critical than ever. IPS provides robust solutions to safeguard your sensitive corporate data and personal information, which are prime targets for cybercriminals aiming to exploit vulnerabilities for financial gain or data theft.
SaaS applications are particularly vulnerable, as they often house critical business data. Threats such as phishing, account takeovers, and data breaches are on the rise, rendering traditional security measures inadequate. IPS applies advanced security protocols, including least privilege access and continuous trust evaluation, to mitigate these risks effectively.
Private applications face increasing threats from cybercriminals looking to exploit weaknesses for corporate espionage, financial theft, or data compromise. Legacy VPN solutions, with their outdated architectures, expose significant vulnerabilities. IPS replaces these with modern, secure access methods that go beyond traditional security models, ensuring comprehensive protection against advanced persistent threats within and outside the network.
With IPS, your organization can confidently protect both SaaS and private applications, ensuring data integrity, privacy, and operational continuity in the face of ever-evolving cyber threats.
Uses Cases
Secure Your SaaS Apps
Gain granular visibility and control over your SaaS applications and cloud services with IPS. Our advanced threat protection stops cyberattacks before they can compromise your data, ensuring your business operations remain secure.
Secure Your Private Apps
Protect your private applications with IPS's Zero Trust Network Access (ZTNA) and comprehensive, layered security. Our solutions ensure only authorized users have access, reducing the risk of unauthorized entry and data breaches.
Protect Your Data
Detect, classify, and prevent unauthorized data exfiltration across any cloud location or app. IPS provides robust data protection to safeguard your sensitive information and maintain regulatory compliance.
VPN Replacement
Upgrade your security by replacing traditional VPNs with IPS's least privilege access controls. Our solution secures both remote and on-premises users, strengthening your overall security posture and reducing the risk of breaches.
How we do it
Least Privilege Access
IPS ZTNA ensures that only authenticated and authorized users can access designated resources. By leveraging user identity, behavior analysis, and contextual information, IPS enforces strict access controls, ensuring resources are accessed only by those who truly need them.
Continuous Monitoring
IPS provides continuous visibility and granular control at the user and device levels. By monitoring application usage, security events, and behavior, IPS dynamically reevaluates security posture, adapting defensive measures in real-time. No implicit trust is given, whether users connect remotely, on-premises, or in a hybrid environment.
Adaptive Micro-Segmentation
IPS prevents lateral movement within the network by implementing adaptive micro-segmentation. This approach dynamically adjusts user and device access based on real-time risk assessments, isolating potential threats and minimizing the risk of an incident escalating into a breach.
Data Leakage Protection
IPS enhances data security by continuously monitoring for and blocking potential data breaches. The platform’s advanced data leakage prevention safeguards sensitive information, ensuring that your data remains secure and compliant with industry regulations.
What you get
Zero Trust Access Enforcement
Implement ZTNA policies across users and devices, applying identity-based controls and continuous monitoring. Versa ensures robust security and compliance by strictly enforcing access policies for all users and devices.
Lateral Movement Prevention
Enhance security between LAN segments with software-defined adaptive micro-segmentation. This prevents lateral movement within your network, limiting the spread of potential threats or unauthorized access between zones.
Advanced Threat Protection
Monitor devices continuously against a wide range of cyber threats, including malware, ransomware, and phishing attacks, ensuring real-time protection against emerging risks.
Digital Experience Monitoring
Monitor and manage device-to-application network performance in real time, ensuring optimal path selection, connectivity, and seamless user experience across your network.
Client-less Security for BYOD and IoT
Include “client-less” IoT and mobile devices in your unified security platform, eliminating security silos and providing comprehensive protection across all endpoints.
Device Identification, Fingerprinting, and Anomaly Protection
Automated device discovery, fingerprinting using 20+ attributes for over 1 million device types, data flow mapping, and posture profiling enable granular security and networking decisions at the device level.
Minimized Risk, Enhanced User Experience, and Streamlined Protection
Simplify administration and cut costs by consolidating security management for both users and devices into one streamlined platform. IPS provides comprehensive, centralized security solutions that reduce complexity and enhance protection across your entire organization.
Minimize your organization’s attack surface, prevent security breaches, block lateral movement, and stop data loss with IPS’s proactive security measures. Safeguard your critical assets and ensure robust protection against evolving cyber threats.
Boost productivity and user satisfaction by ensuring fast, reliable connections to applications. IPS minimizes downtime, optimizes performance, and enhances overall efficiency, creating a seamless and responsive experience for all users.