Cloud Security
IPS cloudPenetration Testing
Utilizing IPS’s Cloud Security Assessment services guarantees a thorough evaluation of your cloud environment, protecting critical assets against sophisticated threats. Consult our cybersecurity experts for more information.
What is CloudPenetration Testing?
Cloud Penetration Testing involves a simulated cyber-attack on systems hosted by cloud providers like AWS, Google Cloud Platform, or Microsoft Azure. The primary objective is to evaluate the security posture of the cloud environment, identify common security misconfigurations, and assess the security of publicly accessible services that could be targeted by malicious actors.
At IPS, we offer comprehensive Cloud Security Assessments tailored for platforms such as AWS, Microsoft Azure, Google Cloud, and similar services. Our assessments cover Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) environments. We focus on identifying vulnerabilities to secure your cloud infrastructure, enhance security measures, and ensure compliance across all cloud service models.
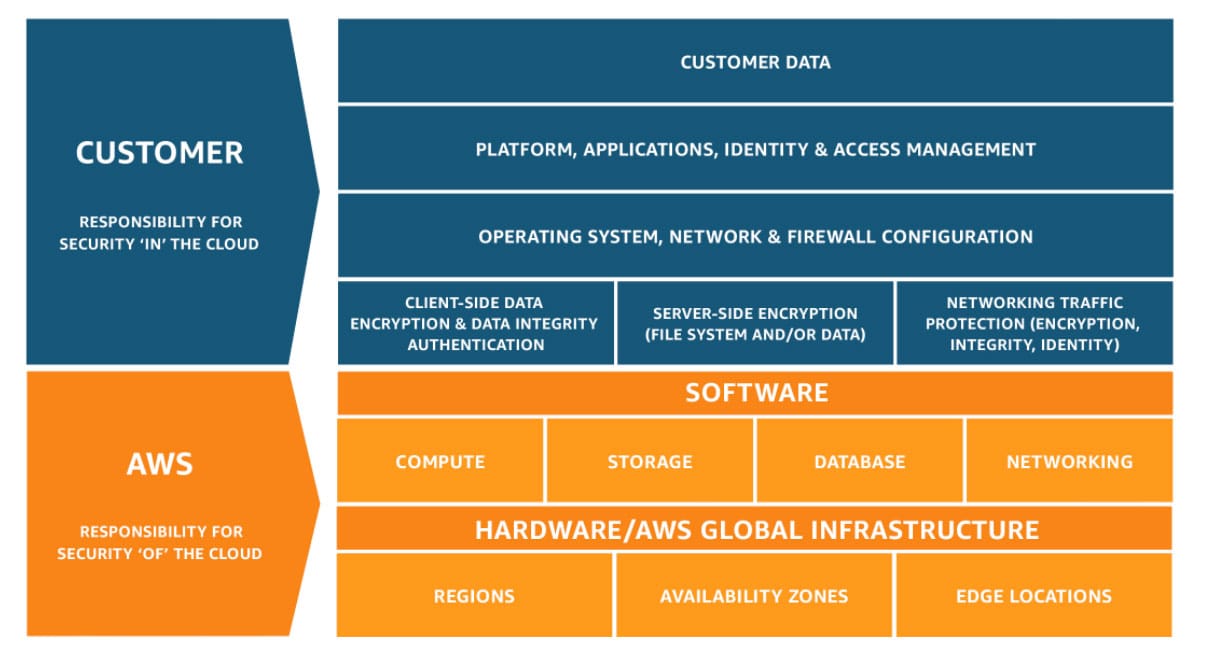
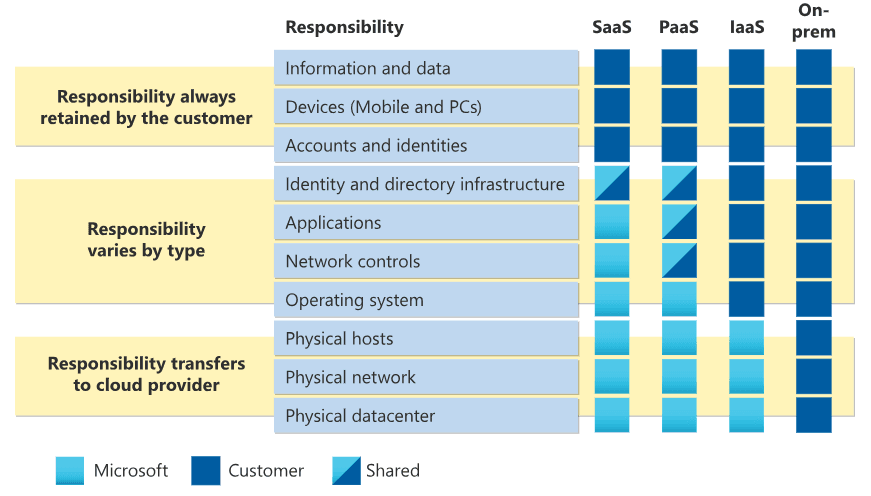
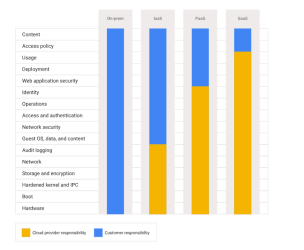
Understanding the Shared Responsibility Model inCloud Computing
Cloud Provider Responsibilities
The provider ensures the security of the cloud infrastructure itself. This includes physical hardware, software, networking, and facilities that run the cloud services. For example, AWS, Google Cloud, and Azure are responsible for securing the servers, storage, and networking equipment in their data centers, as well as the hypervisors that manage virtual machines.
Customer Responsibilities
Customers are responsible for the security of their data and applications within the cloud environment. This involves configuring and managing security settings for their operating systems, applications, and data, as well as ensuring proper identity and access management. For instance, customers need to manage encryption for their data, configure firewalls and access controls, and handle patching and updates for their operating systems and applications.
Key CloudStats to Know
Price vs. Cost
According to IBM, the average cost of a cloud data breach is $4.35 million.
The Importance of Proactive Cloud Penetration Testing
Almost half of all data breaches occur in the cloud.
Cloud Assessment Gaps
Only 20% of organizations assess their cloud security posture in real-time, while 58% report assessing their environments less than once a month.
What Will be Assessed
IAM Access Analyzer
Analyze and validate IAM Access Analyzer findings to ensure that permissions granted by policies are appropriately scoped. Test for any unintended access paths that could expose sensitive resources.
AWS - IAM
Evaluate IAM roles, policies, and permissions to identify overly permissive access or potential privilege escalation. Test for compliance with the principle of least privilege and ensure that policies are correctly applied to users and groups.
AWS Config
Assess AWS Config rules and compliance reports for any misconfigurations or policy violations. Test the effectiveness of automated compliance checks and the response to detected configuration changes.
AWS CloudTrail
Evaluate CloudWatch monitoring configurations for all critical resources. Test alerting and monitoring setups to ensure that anomalies are detected and responded to in a timely manner.
AWS VPC
Assess VPC configurations, including subnets, route tables, and network ACLs, to identify potential vulnerabilities. Test the segmentation and isolation of sensitive network resources and verify proper setup of security groups and firewall rules.
AWS S3 and EC2
For S3, test bucket permissions, encryption settings, and data access controls. For EC2, evaluate instance configurations, security groups, and key management practices to ensure they adhere to security best practices.
Identity Management
Assess Azure Active Directory (AD) for user and group management practices. Test for proper application of role-based access control (RBAC) and verify that multi-factor authentication (MFA) is enforced where necessary.
Network Security
Evaluate Azure Network Security Groups (NSGs), application security groups, and firewalls for misconfigurations and vulnerabilities. Test network segmentation and inbound/outbound traffic controls.
Logging and Threat Detection
Evaluate Azure Monitor and Log Analytics configurations for completeness and effectiveness. Test for proper setup of alerting mechanisms and the ability to detect and respond to security incidents.
Data Protection
Review data encryption methods for Azure services, including data at rest and in transit. Test backup and recovery procedures for critical data and ensure compliance with data protection policies.
Endpoint Security
Evaluate the security of endpoints managed through Azure Security Center and Microsoft Defender. Test for proper configuration of endpoint protection policies and threat detection capabilities.
Incident Response
Assess Azure Security Center’s incident response capabilities. Test the integration of incident response workflows and the effectiveness of automated response actions.
Backup and Recovery
Review Azure Backup configurations and test recovery procedures for critical data. Ensure that backup policies are correctly applied and that data can be restored as needed.
Identity and Access Management
Review IAM roles and policies for Google Cloud resources. Test for adherence to the principle of least privilege and validate that permissions are correctly assigned.
Logging and Monitoring
Assess Google Cloud Logging and Monitoring configurations for coverage and effectiveness. Test for proper setup of alerts and responses to detected anomalies.
Virtual Machine Instances
Review VM instance configurations for security best practices. Test access controls, instance security settings, and patch management practices.
Kubernetes Engine
Review security settings for Google Kubernetes Engine (GKE), including cluster configurations, role-based access control (RBAC), and network policies. Test for proper isolation and security of containerized applications.
Storage Security
Assess security settings for Google Cloud Storage, including bucket permissions, encryption, and access controls. Test for proper configuration and protection of stored data.
Cloud SQL Database
Evaluate security configurations for Cloud SQL instances. Test for proper access controls, encryption settings, and database security measures.
Virtual Networking
Evaluate Google Cloud VPC configurations, including firewall rules, subnets, and network tags. Test for proper network segmentation and access controls.
Our TestingMethodology
Scoping and Planning: We begin by defining the scope, objectives, and specific areas of focus for the penetration test based on your cloud environment (AWS, Google Cloud, Azure) and security concerns.
Reconnaissance and Vulnerability Identification: Our team collects information about your cloud assets and identifies vulnerabilities using automated tools and manual techniques, focusing on misconfigurations, weak access controls, and other security issues.
Exploitation and Attack Simulation: We simulate real-world attack scenarios to exploit identified vulnerabilities, assessing the potential impact on your systems and data, while strictly adhering to ethical guidelines.
Reporting and Documentation: We provide a detailed report that includes identified vulnerabilities, risk assessments, and prioritized remediation recommendations, ensuring clarity and actionable insights.
Post-Testing Support and Remediation
Debrief and Custom Remediation Plan: We hold a debriefing session to discuss findings and provide a tailored remediation plan. Our experts offer consultative guidance on implementing best practices and securing your cloud infrastructure.
Technical Assistance and Re-Testing: We assist with the remediation process and conduct re-tests to confirm that vulnerabilities have been effectively addressed, ensuring your security measures are robust.
Continuous Improvement and Training: We support your ongoing security efforts by offering recommendations for continuous improvement, regular assessments, and training for your internal teams on secure cloud practices and incident response.
The Benefits of Conducting Cloud Penetration Testing?
Identifies Vulnerabilities
Cloud penetration testing helps uncover security weaknesses and misconfigurations across your cloud environments (AWS, Google Cloud, Azure). By simulating real-world attacks, it identifies potential entry points that attackers could exploit, such as misconfigured permissions, insecure API endpoints, or vulnerable applications. Addressing these vulnerabilities before they can be exploited ensures that your cloud infrastructure remains secure and resilient against threats.
Ensures Compliance
Many industries require adherence to strict regulatory standards and security frameworks (e.g., GDPR, HIPAA, PCI-DSS). Cloud penetration testing helps demonstrate compliance by validating that your cloud environments are configured according to required security controls and best practices. This not only helps avoid potential fines and legal issues but also builds trust with clients and stakeholders by showing that you take data protection seriously.
Enhances Security Posture
Regular penetration testing provides comprehensive insights into your cloud security measures, highlighting areas that need improvement. By identifying gaps in your security posture, such as inadequate firewall rules or insufficient encryption practices, the testing helps you strengthen your defenses. This proactive approach improves your ability to protect critical data and applications from sophisticated attacks, enhancing your overall security posture.
Protects Sensitive Data
Ensuring the security of sensitive data in the cloud is crucial for maintaining confidentiality and integrity. Cloud penetration testing evaluates how well your data protection measures, such as encryption and access controls, are implemented. By identifying weaknesses that could lead to data exposure or breaches, you can strengthen your data security practices and safeguard your valuable information from unauthorized access or theft.
Prepares for Real-World Attacks
Penetration testing simulates actual attack scenarios to test your cloud infrastructure's resilience. This realistic approach helps evaluate your incident response plans, refine your security strategies, and ensure that your team is prepared to handle real-world attacks. By identifying how your systems respond to simulated breaches, you can make informed improvements and better prepare for potential security incidents.
Why Choose IPS for Web Application Penetration?
At IPS, we offer continuous scanning and monitoring to complement our manual web application penetration tests. Our approach reduces your attack surface and ensures ongoing protection. We meticulously review all scan results to eliminate false positives, validate vulnerabilities with real-world exploits, and combine multiple weaknesses to create more significant attack vectors.
By choosing IPS for your external penetration testing, you benefit from comprehensive, proactive security measures that guard against emerging threats. Our expert team employs advanced techniques and technologies to uncover vulnerabilities and provide actionable insights, keeping your defenses robust and current.
Partner with IPS for a commitment to maintaining top-tier cybersecurity standards for your organization.