Application Security
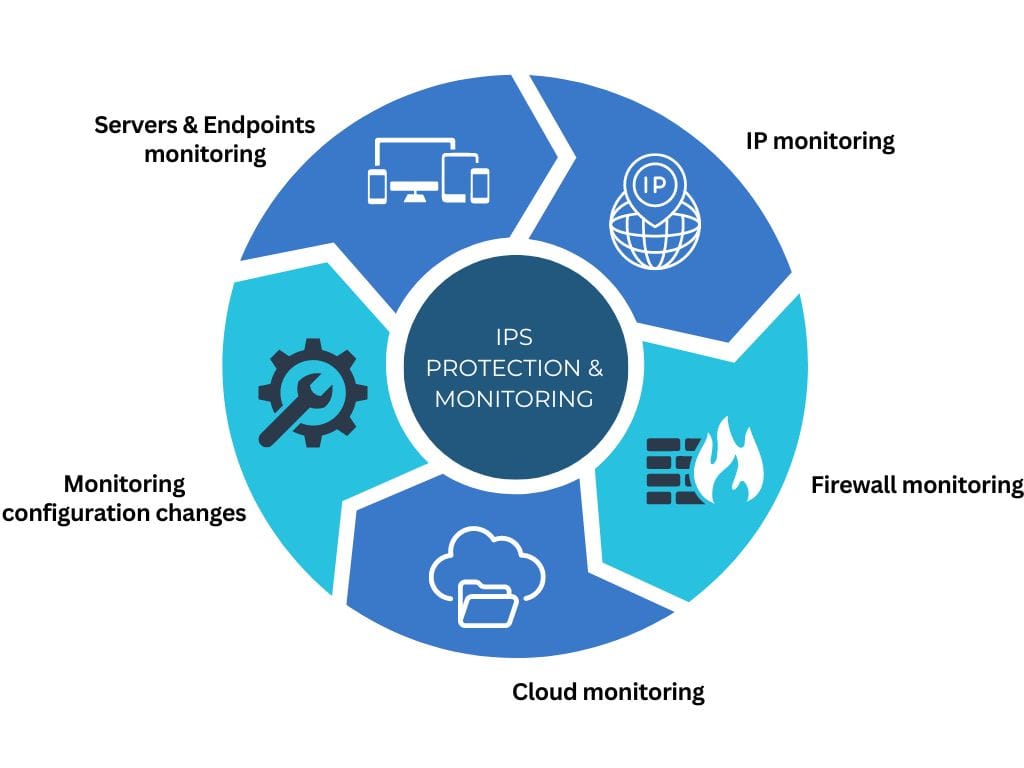
IPS EndpointProtection & monitoring
IPS specializes in delivering world-class security solutions to the SMB space. Our services provide a cost-effective answer to the ever-evolving world of cyber threats.
What Is Cyber Security Monitoring?
IPS security monitoring is an automated process that helps organizations identify cyber threats through continuous and rigorous observation of network traffic, endpoint behavior, servers, logs, and more. When suspicious activity is detected, IPS monitoring tools alert the IT team, prompting an immediate response. This proactive approach ensures that cyber-attacks are stopped and mitigated before any damage can occur.
To effectively monitor and protect IT infrastructure against cyber attacks, several key components must be safeguarded. Here’s a comprehensive overview of the IT infrastructure elements that should be monitored and protected:
Network Infrastructure
- VPN
- ISP
- Firewalls
- Routers and Switches
- Network Traffic
Servers and Endpoints
- Operating Systems
- Application Servers
- Workstations and Laptops
- Mobile Devices
Cloud Infrastructure
- Cloud Access Controls
- Virtual Machines
- Cloud Storage
Applications and Databases
- Web Applications
- Databases
- APIs
Identity and Access Management
- User Accounts
- Authentication Systems
- Privilege Management
Security Information and Event Management (SIEM)
- Log Management
- Event Correlation
- DNS
Backup and Recovery
- Backup Systems
- Disaster Recovery Plans
IPS Cybersecurity Monitoring
1. Endpoint Monitoring
Cybersecurity monitoring employs real-time response to help organizations identify threats more swiftly and effectively.
These threats often stem from active cyber-attacks or vulnerabilities within the system. To address these challenges, cybersecurity monitoring relies on two main categories: endpoint monitoring and network monitoring.
- Malware Activity: Detecting and analyzing suspicious software.
- System Behavior: Monitoring unusual or unauthorized changes.
- File Integrity: Checking for unauthorized modifications or deletions of critical system and application files.
- System Behavior: Monitoring unusual or unauthorized changes.
- Event Logs: Collecting and analyzing logs from endpoints to identify and investigate security incidents or policy violations.
- Security Updates: Ensuring that endpoints are up-to-date with the latest security patches and updates.
- Configuration Changes: Monitoring changes in system configurations or security settings to identify potential security risks or misconfigurations.
- Access Permissions: Monitoring changes in system configurations or security settings to identify potential security risks or misconfigurations.
- User Activity: Tracking user actions, including login attempts, access to sensitive data, and usage patterns, to identify potential insider threats or compromised accounts.
2. Network Monitoring
Similarly, network monitoring involves the supervision, tracking, and analysis of an entire network to prevent cyber threats.
Networks can have flawed components that lead to performance issues—such as slow webpage loading or site crashes—that might indicate underlying vulnerabilities. Network monitoring addresses these challenges by continuously observing network traffic, activity logs, and more.
Examples of network monitoring tools include SIEM systems, Intrusion Detection Systems (IDS), and Behavioral Analytics (BA) systems. The combination of endpoint and network monitoring forms the foundation of effective cybersecurity services. Now, let’s explore why these observational tools are crucial for organizations.
Inbound Monitoring:
- Traffic Analysis: Monitoring unusual or unauthorized changes.
- Intrusion Detection: Monitoring for signs of unauthorized access attempts or breaches from external sources.
- Intrusion Detection: Monitoring for signs of unauthorized access attempts or breaches from external sources.
- Firewall Logs: Monitoring for signs of unauthorized access attempts or breaches from external sources.
- Malware Detection: Identifying malicious payloads or suspicious files entering the network through various protocols.
- IP Reputation: Checking incoming IP addresses against known threat databases to identify potentially harmful sources.
Outbound Monitoring:
- Traffic Analysis: Analyzing outgoing traffic for unusual patterns or data exfiltration attempts.
- Data Leakage: Monitoring for unauthorized transmission of sensitive information or large volumes of data to external destinations.
- Connection Monitoring: Tracking connections to external servers or IP addresses to detect potential command-and-control communications or other threats.
- Firewall Logs: Reviewing logs for outgoing traffic to ensure that communications are legitimate and comply with security policies.
- Application Behavior: Observing the behavior of applications and services to detect unauthorized or anomalous data transmissions.
3. Database Monitoring
At IPS, we understand that effective database monitoring is crucial for maintaining optimal performance and security. Our all-in-one platform encompasses various methodologies to ensure comprehensive system oversight, focusing on key aspects such as performance, availability, security, and log analysis.
- Performance Monitoring
Our platform provides in-depth analysis of critical database metrics, including response times, query execution efficiency, and resource utilization. By optimizing these parameters, we help achieve high performance and enhance user satisfaction. Availability Monitoring
With our availability monitoring features, we ensure your database remains operational 24/7. By proactively addressing accessibility factors, we minimize downtime and maintain consistent user access, allowing your business to run smoothly.Logs Monitoring
Our logs monitoring tools analyze database-generated logs to identify patterns, anomalies, and significant events. This capability aids in diagnosing issues, understanding user behavior, and optimizing overall performance.
4. Supply Chain Monitoring
The safety of your supply chain is critical to the success of your business.
IPS Supply Chain Risk Management, powered by EvolveSC, simplifies and automates your risk assessments, providing real-time insights into threats like exposed credentials, dark web activity, and system vulnerabilities. With 24/7 continuous monitoring, IPS identifies security gaps across third-party vendors without requiring manual intervention. Through automated pen testing and real-time exploit detection, IPS helps businesses proactively secure their supply chain, reduce risks, and protect critical data.
Our intelligent, scalable platform empowers you to make informed decisions, build trust, and confidently manage vendor relationships while ensuring business growth.
Key Features:
- Leaked credentials detection
- Dark web monitoring
- Real-time exploit identification
- Automated pen testing
Benefits of Cyber Security Continuous Monitoring with IPS
Continuous cybersecurity monitoring offers significant benefits for strengthening your network defenses, including:
Significant Reduction in Cyber Attacks:
A fortified security perimeter effectively prevents cyber-attacks and limits the damage when breaches occur. Real-time monitoring allows for rapid threat mitigation, minimizing potential harm.
Increased Employee Productivity
Network monitoring tools help track and optimize employee productivity by ensuring systems operate efficiently. By scanning for vulnerabilities, these tools also contribute to smoother network performance, which enhances overall productivity.
Regulatory Compliance:
Continuous monitoring safeguards data integrity and helps prevent breaches, ensuring adherence to industry regulations. This reduces the risk of penalties and boosts your brand’s reputation and customer trust.
Advanced Threat Intelligence:
Ongoing monitoring builds a repository of threat intelligence, enabling faster detection of malware and anomalies. This proactive approach enhances future network security and continuously adapts to emerging threats.
Tech Stack that Powers your Triumph





Choosing IPS for Your Cyber Security Monitoring
IPS Next-Generation Firewall
IPS: Leading the Way in Cybersecurity and Cloud Computing Solutions
At IPS, we are dedicated to delivering innovative and effective cybersecurity and cloud computing solutions to ensure the best security posture for your organization.
Our suite of advanced security platforms offers superior protection and monitoring services. Here are some of the highlights of what IPS brings to the table:
IPS Cyber Command
Our IPS Cyber Command (NDR) Platform provides comprehensive monitoring for malware, security events, and potential future threats. Equipped with advanced AI algorithms, this platform keeps you informed about vulnerabilities and emerging threats, ensuring your network remains secure and resilient.
IPS Endpoint Secure
Our AI-powered IPS Next-Generation Firewall (NGFW) provides cutting-edge protection for both your network and endpoints. Leveraging advanced malware detection with Neural-X and Engine Zero, our NGFW delivers comprehensive threat defense with intuitive management. Experience swift and effective threat mitigation with IPS’s state-of-the-art firewall technology.
Advanced Threat Detection and Response
At IPS, we offer a range of advanced threat detection and response tools that work in unison to maintain the highest security standards. Our solutions are designed to be effective, efficient, and affordable, providing you with the best in cybersecurity and cloud computing.
IPS Incident Response
IPS Incident Response delivers flexible, fast, and effective solutions for eliminating and preventing cyber-attacks. Our incident response services focus on threat detection, eradication, and active disaster recovery, providing tailored analysis and strategies to safeguard your business against future attacks.